Verify Runtime of Upgrade
Finding the Proposal#
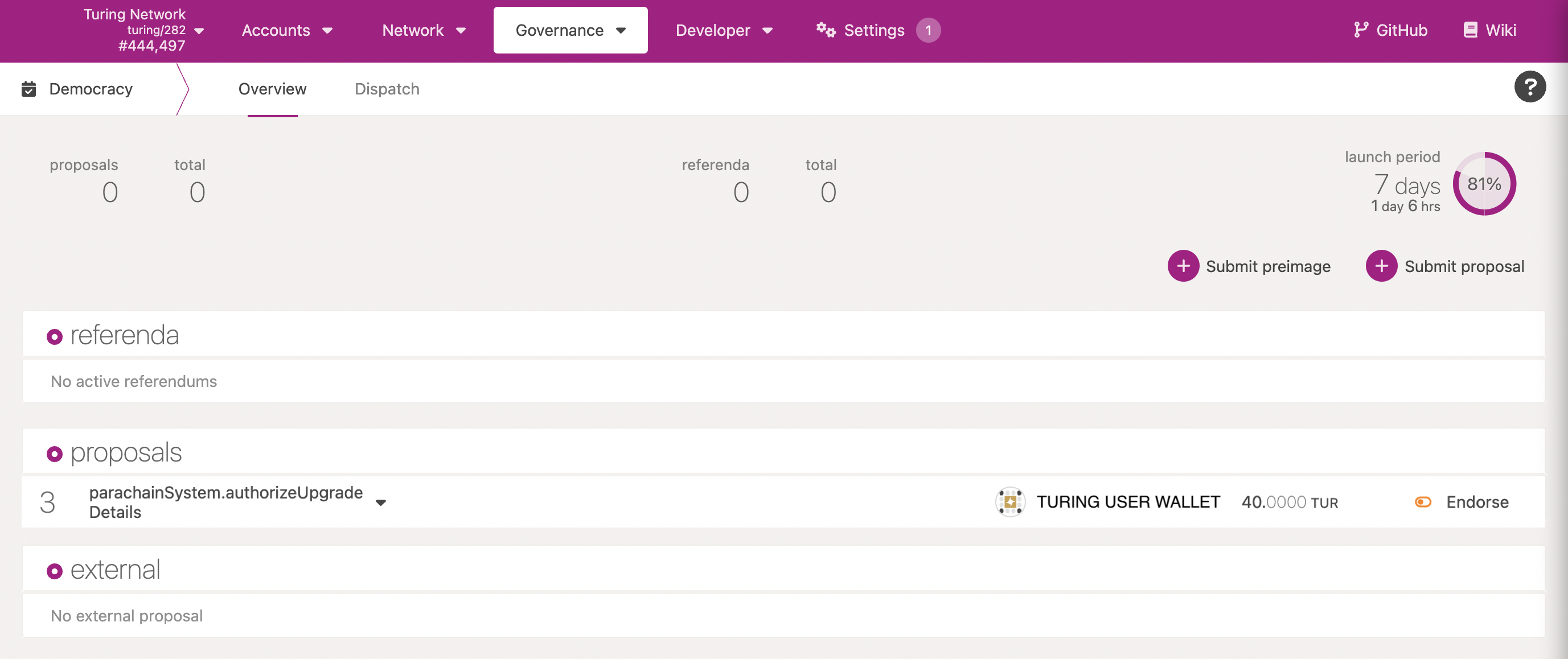
To find the proposed runtime upgrade navigate to Turing's Democracy page. If a runtime upgrade has been proposed you will see a proposal under the proposals section for parachainSystem.authorizeUpgrade as shown in the image below. For this example we are using a proposed runtime upgrade to v1.8.0.
Upgrade Preimage Information#
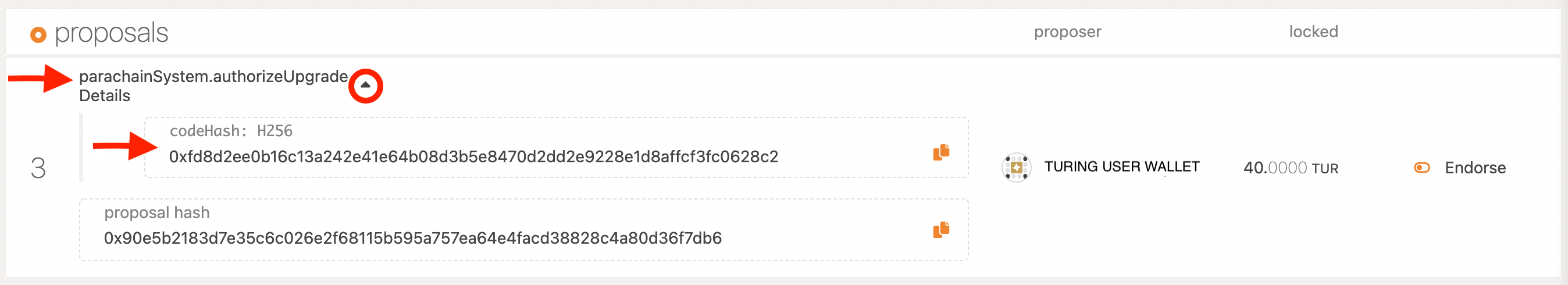
Once you have identified the proposal click on the arrow next to parachainSystem.authorizeUpgrade and expand for more details. There you will see the H256 code hash for the corresponding release version v1.8.0.
0xfd8d2ee0b16c13a242e41e64b08d3b5e8470d2dd2e9228e1d8affcf3fc0628c2
Verify Code#
The necessary information to verify the code can be found in the corresponding release page on Github. The release page for v1.8.0 can be found here. To view previous releases you can navigate here.
First, you will want to verify the BLAKE2_256 hash in the release notes matches the proposal codeHash from the previous section. Next, you can build your own WASM runtime to compare with the proposed upgrade.
Build WASM Runtime for the Release#
- Install srtool.
- Follow the directions in OAK-blockchain repository to build from source.
- Checkout release branch.
git clone git@github.com:OAK-Foundation/OAK-blockchain.git
git fetch --all --tags
git checkout tags/v1.8.0 -b branch-1.8.0
Switched to a new branch 'branch-1.8.0'
- Build release with srtool.
srtool build --package turing-runtime
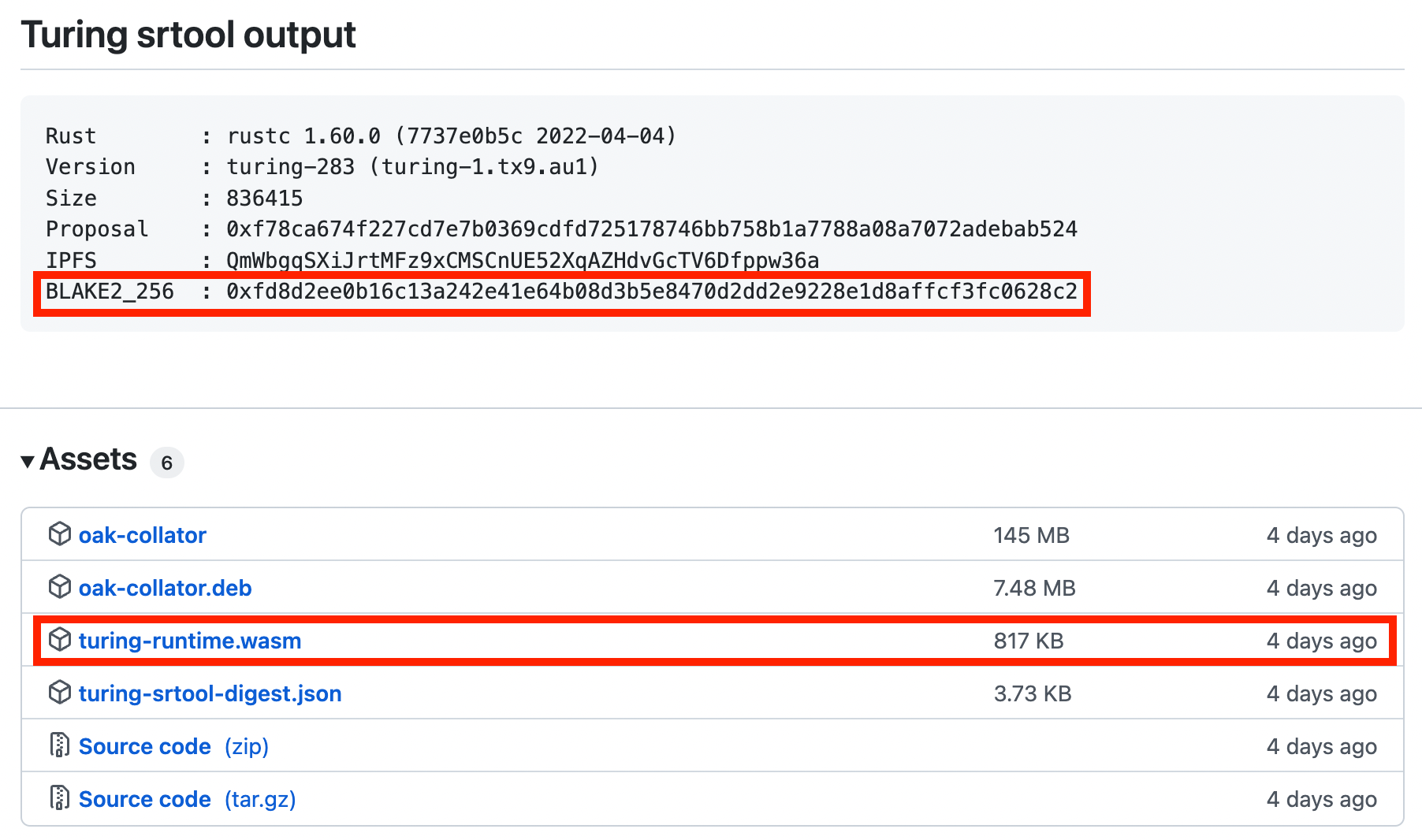
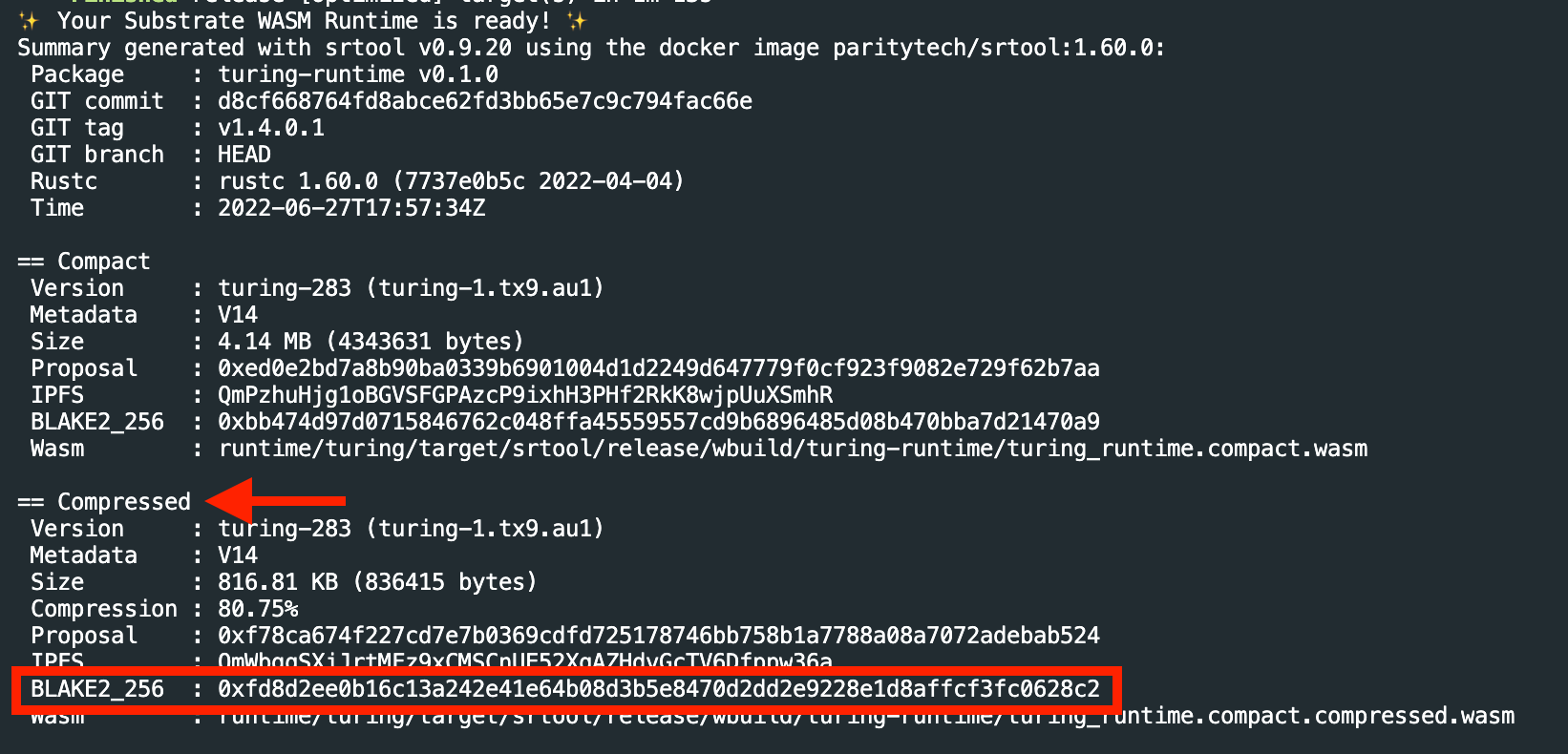
- Make note of
BLAKE2_256hash of thecompressedWASM after the srtool completes building.
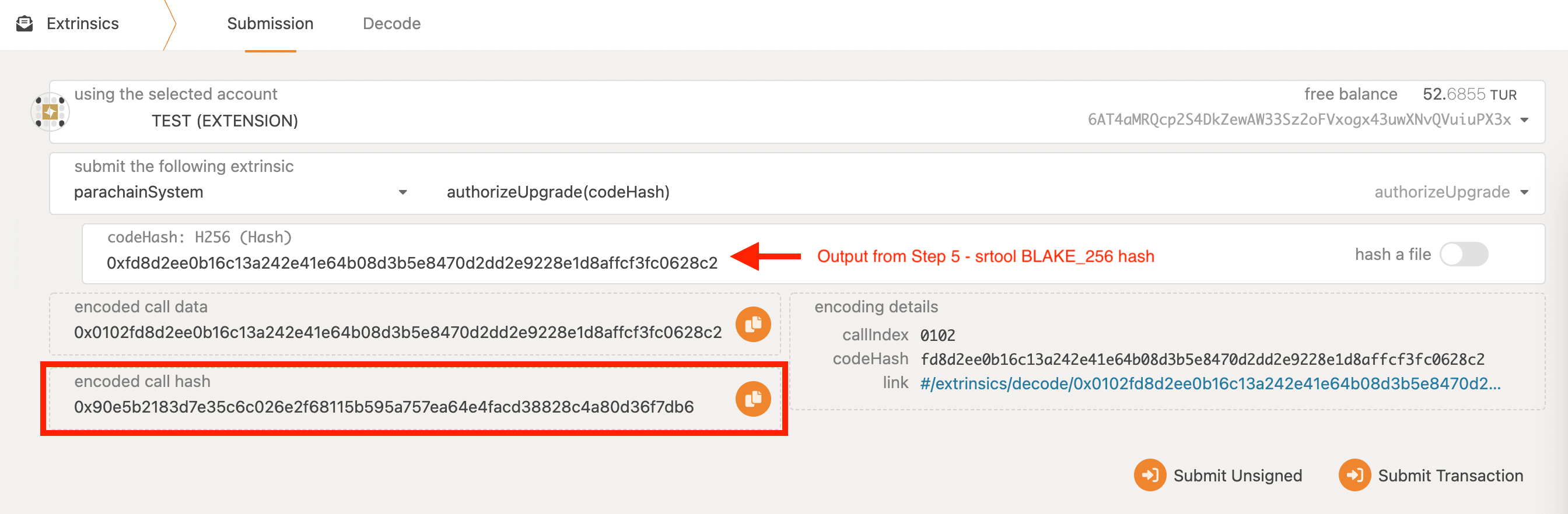
Compare Hash#
Navigate to the Developer - Extrinsics tab. Use the parachainSystem extrinsic to authorizeUpgrade as shown in the image below. Paste the BLAKE2_256 hash noted in step 5 above into the codeHash field. Compare the encoded call hash and ensure it matches the proposal hash found in the first section of this document, Finding the Proposal.